41 security labels access control
Security Labels and Mandatory Access Control (MAC) - IBM Security Labels and Mandatory Access Control (MAC) ... Mandatory Access Control (MAC) is a security policy that governs which subjects can access which objects, ... Comparing Access Control: RBAC, MAC, DAC, RuBAC, ABAC - TechGenix Mar 30, 2022 · Types of Access Control. Access control is one of the easiest and most effective ways to meet your security needs. Yet, not all techniques work the same way. In this section, I’ll go through the 5 main types of access control you’ll run into. 1. Mandatory Access Control (MAC) Above all others, MAC is the most strictly enforced control method.
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Article - CS320673 [Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label Modified: 24-Aug-2022 Applies To Windchill PDMLink 10.0 to 12.0 Windchill ProjectLink 10.0 to 12.0 Pro/INTRALINK 8.x + 10.0 to 12.0 Windchill PDM Essentials 10.0 to 12.0 PTC Arbortext Content Manager 10.0 to 12.0 Description How to manage access control?
Security labels access control
Access Control | OWASP Foundation Access Control, also known as Authorization — is mediating access to resources on the basis of identity and is generally policy-driven (although the policy may be implicit). It is the primary security service that concerns most software, with most of the other security services supporting it. Access control - Wikipedia In the fields of physical security and information security, access control (AC) is the selective restriction of access to a place or other resource, while access management describes the process.The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.. Locks and login credentials are two analogous mechanisms of access control. Secure external collaboration using sensitivity labels In addition to that, it is possible to make the protected content time-bound as well as control whether users can access it offline and for how long. In this case your label may look like this: Figure 3: A sensitivity label granting Authenticated users view-only access.
Security labels access control. Access Control using Security Labels & Security Clearance - Isode Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form. Setting Access Control Permissions for Agreement Managers - PTC Read permission is required to access any object and view its information page. The following table illustrates additional access control permissions required for actions often completed by an agreement manager. The object location column has the following values. Use these values to determine the domain in which to grant access control ... Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access. Introduction to Oracle Label Security Oracle Label Security enables application developers to add label-based access control to their Oracle9iapplications. It mediates access to rows in database tables based on a label contained in the row, and the label and privileges associated with each user session.
PostgreSQL: Documentation: 14: SECURITY LABEL PostgreSQL places no restrictions on whether or how a label provider must interpret security labels; it merely provides a mechanism for storing them. In practice, this facility is intended to allow integration with label-based mandatory access control (MAC) systems such as SELinux. Such systems make all access control decisions based on object ... Conditional Access and Access Control – Azure AD | Microsoft Security 25.02.2021 · This security policy enforcement engine analyzes real-time signals to make security enforcement decisions at critical checkpoints. The left side of the diagram represents how signals from users, devices, locations, apps, data labels, and risk analysis are aggregated; decisions are enforced based on the aggregated signals. Security-labels - FHIR v4.3.0 - Health Level Seven International A security label is a concept attached to a resource or bundle that provides specific security metadata about the information it is fixed to. The Access Control decision engine uses the security label together with any provenance resources associated with the resource and other metadata (e.g. the resource type, resource contents, etc.) to Security Labels and Access Control - PTC Support Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not ...
Which type of access control model assigns security level labels to ... discretionary attribute-based Explanation: Mandatory access control (MAC) assigns security level labels to information and enables users with access based on their security level clearance. This is the strictest access control and is typically used in military or mission critical applications. Apply encryption using sensitivity labels - Microsoft Purview ... Use the following options to control who can access email or documents to which this label is applied. You can: Allow access to labeled content to expire, either on a specific date or after a specific number of days after the label is applied. After this time, users won't be able to open the labeled item. Define access control list and capability list and compare them ... The Discretionary Security Property: use of an access matrix to specify the discretionary access control. SE Linux, like most other systems that protect multi-level data, uses the BLP model. This model specifies how information can flow within the system based on labels attached to each subject and object. Types of Access Control - Rule-Based vs Role-Based & More - Genea An example of role-based access control is if a bank's security system only gives finance managers but not the janitorial staff access to the vault. ... a system administrator configures access policies and defines security permissions. Labels contain two pieces of information—classification (e.g., "top secret") and category (e.g ...
Mandatory Access Control - Trusted Extensions User's Guide - Oracle Mandatory access control (MAC) is a system-enforced access control mechanism that is based on label relationships. The system associates a sensitivity label with all processes that are created to execute programs. MAC policy uses this label in access control decisions.
Access Control | OWASP Foundation Access Control, also known as Authorization — is mediating access to resources on the basis of identity and is generally policy-driven (although the policy may be implicit). It is the primary security service that concerns most software, with most of the other security services supporting it.
Security - FHIR v4.3.0 - Health Level Seven International Two of the classic Access Control models are: Role-Based Access Control (RBAC), and Attribute-Based Access Control (ABAC). In Role-Based Access Control (RBAC), permissions are operations on an object that a user wishes to access. Permissions are grouped into roles. A role characterizes the functions a user can perform. Roles are assigned to users.
Mandatory Access Control - an overview | ScienceDirect Topics Mandatory Access Control ( MAC) is system-enforced access control based on subject's clearance and object's labels. Subjects and objects have clearances and labels, respectively, such as confidential, secret, and top secret. A subject may access an object only if the subject's clearance is equal to or greater than the object's label.
Controlling Access to the Kubernetes API | Kubernetes 09.07.2022 · This page provides an overview of controlling access to the Kubernetes API. Users access the Kubernetes API using kubectl, client libraries, or by making REST requests. Both human users and Kubernetes service accounts can be authorized for API access. When a request reaches the API, it goes through several stages, illustrated in the following diagram: …
Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to ...
Mandatory access control - Wikipedia Access to the labels and control mechanisms are not [citation needed] robustly protected from corruption in protected domain maintained by a kernel. The applications a user runs are combined with the security label at which the user works in the session. Access to information, programs and devices are only weakly controlled [citation needed].
Security: Access Control - Bosch Security and Safety Systems I Global Getting a connection error when accessing the AEC webpage When trying to access the Access Easy Controller via Microsoft Edge, Chrome or other web browsers, you may get an error, "the connection for this site is not secure", which prevents you from connecting to the AEC. No ratings 369 0 03-30-2022 Can I downgrade my AEC firmware to 2.1.8.5?




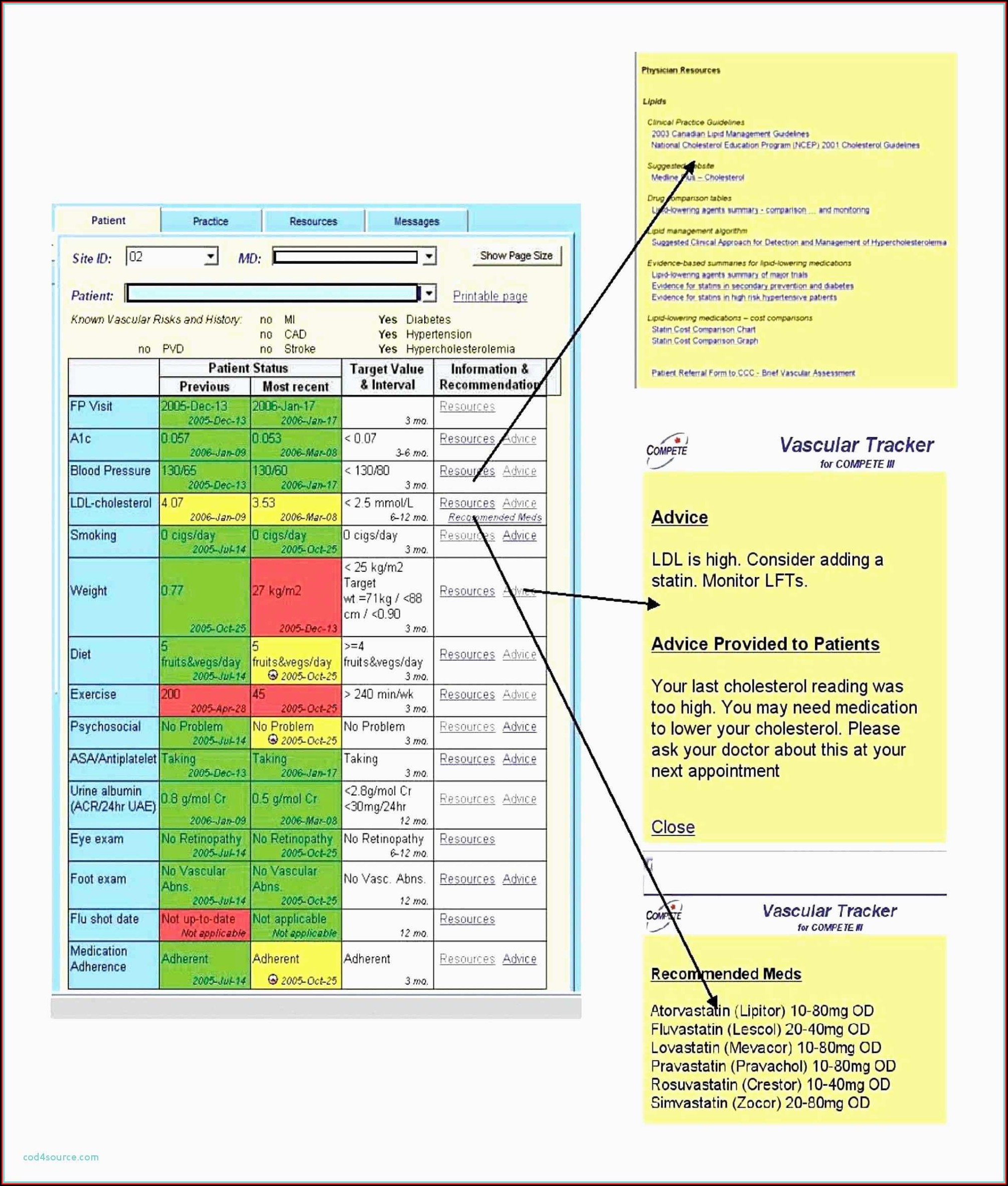


Post a Comment for "41 security labels access control"